Learning Objectives:
You will be able to identify possible security issues with JavaScript
Homework:
Play with AJAX
Topics Covered:
End of Semester for Message for CIS166 Web Scripting Class
.
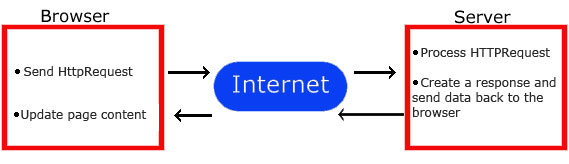
AJAX = Asynchronous JavaScript and XML. (Marketing term designed to sell books and services)
XMLHttpRequest object (to exchange data asynchronously with a server)
JavaScript/DOM (to display/interact with the information)
CSS (to style the data)
XML (often but not allways used as the format for transferring data)
The beauty of AJAX is the ability to update part of a web page - without reloading the whole page.
Examples:
Fill in the State using AJAX
Trouble Shooting Errors:
The try statement lets you to test a block of code for errors while it is being executed.
The catch statement allows you to define a block of code to be executed, if an error occurs in the try block.
The throw statement lets you create custom error messages.
When an error occurs, when something goes wrong, the JavaScript engine will normally stop, and generate an error message. The technical term for this is: JavaScript will throw an error.
.
Security
JavaScript does not provide any way to write or delete files on the client computer! (no file object and no file access functions). Javascript is given a sandbox (restricted area on your computer)
O'Reilly Books' JavaScript: The Definitive Guide describes the restricted features and the Same-origin Policy that limits the capabilities of Javascript and browser interactions.
AJAX adds another security concern with its ability to bypass firewall restrictions with the http request object.
Web Application Security
Protect your password (don't give it to anyone), update your Server's Operating System with the latest patches and set permissions properly.
Security Client Side(FireFox Security & Microsoft Security)
Builder.Com JavaScript Security& Windows Security
CERT® Coordination Center Carnegie Mellon University's Computer Emergency Response Team
Computer Security, and FBI Cyber Crimes
CIAC Security Web site Must check regularly Web site!!!
CSRC Computer Security Resource CenterCERT® Coordination Center Carnegie Mellon University's Computer Emergency Response Team
.
Terms:
A security policy is simply a set of rules governing what scripts can do, and under what circumstances.
Same-origin Policy: Scripts will run or access only on the server of origin.
“Sandbox” environment: Scripts run in a protected environment in the browser.
Patches, Viruses and Vulnerabilities
.